06-04-2023, 09:00 AM
Types of Attacks and Used Techniques
Mini-FAQ on commonly seen DDoS attacks today.
Currently, the most popular attacks are amplifications, based on the principle of "amplification." In simple terms, the attacker spoofs the IP address of the target and sends requests to DNS, NTP, and other servers using that IP. Consequently, the server responds with packets of significantly larger sizes. To put it bluntly, sending 1 byte results in receiving 30-60 bytes in response. The more requests made to different services and the higher their quantity, the more powerful the attack becomes. Currently, amplification attacks range in strength from 1 to 30 Gbps. This method is widely used due to its affordability.
However, the good news is that such attacks are "dumb" and can be easily blocked by having the necessary resources for it.
The main types of amplifications are:
The attacks described above are primarily blocked at the ISP and data center level. Blocking them on the server itself is pointless unless you have a minimum of several gigabits of bandwidth.
Amplification Coefficient Table:
![[Image: 000001.jpg]](https://fullserver.su/forum/images/random/000001.jpg)
Mini-FAQ on commonly seen DDoS attacks today.
Currently, the most popular attacks are amplifications, based on the principle of "amplification." In simple terms, the attacker spoofs the IP address of the target and sends requests to DNS, NTP, and other servers using that IP. Consequently, the server responds with packets of significantly larger sizes. To put it bluntly, sending 1 byte results in receiving 30-60 bytes in response. The more requests made to different services and the higher their quantity, the more powerful the attack becomes. Currently, amplification attacks range in strength from 1 to 30 Gbps. This method is widely used due to its affordability.
However, the good news is that such attacks are "dumb" and can be easily blocked by having the necessary resources for it.
The main types of amplifications are:
- DNS - Packets arrive with source port 53 (UDP) To block these attacks, all UDP packets with source port 53 are trimmed, except for the IP addresses of DNS servers used by the server (eg, 8888)
- NTP - Packets arrive with source port 123 (UDP) Blocking is similar to DNS attacks, possibly without allowing specific IP addresses if you don't use internet time synchronization
- SSDP - Packets arrive with source port 1900 (UDP) Blocking UDP Source Port 1900
- CHARGEN - Packets arrive with source port 19 (UDP) Blocking UDP Source Port 19
- SNMP - Packets arrive with source port 161 (UDP) Blocking UDP Source Port 161
- QOTD - Packets arrive with source port 17 (UDP) Blocking UDP Source Port 17
- TeamSpeak - Packets arrive with source port 9987 (UDP) Blocking UDP Source Port 9987
- NetBios - Packets arrive with source port 137 (UDP) Blocking UDP Source Port 137
- Quake 3 - Packets arrive with source port 27690 (UDP) Blocking UDP Source Port 27690
- Steam - The majority of packets arrive with source port 27015 (UDP) Blocking UDP Source Port 27015
- This type of attack cannot be classified as amplification and is primarily used by certain botnets However, it is still popular for attacks on HLDS servers, with source port 0 (UDP) Blocking UDP Source Port 0
The attacks described above are primarily blocked at the ISP and data center level. Blocking them on the server itself is pointless unless you have a minimum of several gigabits of bandwidth.
Amplification Coefficient Table:
![[Image: 000001.jpg]](https://fullserver.su/forum/images/random/000001.jpg)
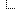


![[-]](https://fullserver.su/forum/images/collapse.png)
